Be careful, the source code you’re reading is not necessarily the code to be executed. Security researchers at the University of Cambridge have just uncovered an attack called “Source Trojan” which allows malicious code to be embedded in source code that to the naked eye appears completely normal, regardless of the underlying language.
In fact, the researchers have successfully tested their method for C, C++, C#, Javascript, Java, Rust, Go, and Python languages. The source of the Trojan horse is also a massive attack on the supply chain. Back door hidden in unit open source It can be found as in all software that would integrate it. However, some bricks open source It is used in many programs. So the possibility of publishing is very large.
Also to discover the video:
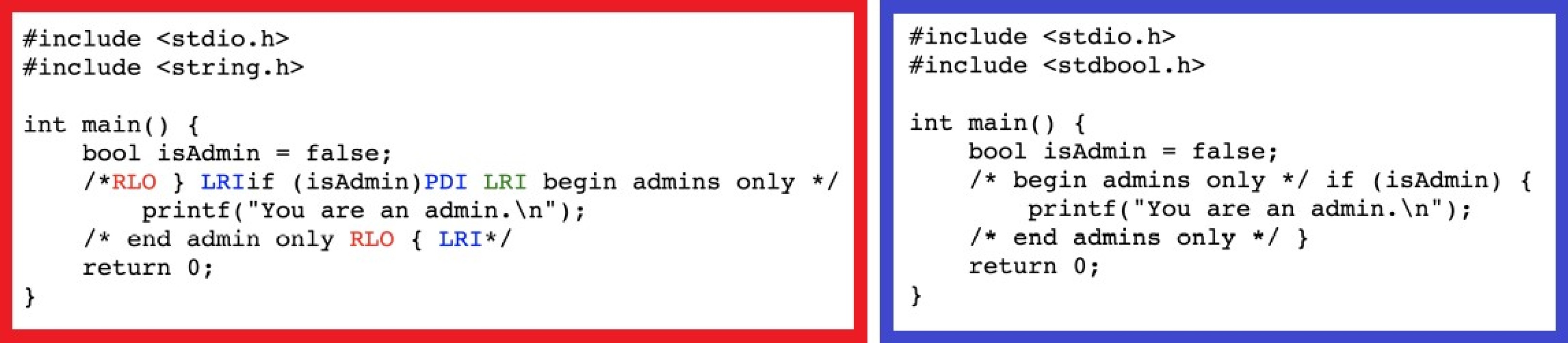
How is this possible? The source of the Trojan horse is based on the fact that you can refer to different directions in the same ciphertext in the Unicode standard. This allows, for example, to display the quote correctly in Arabic or Hebrew within a French text. These changes in direction are made using invisible characters called “Bidi”. The letters “LRI” and “RLI” respectively indicate that the following words should be displayed from left to right, or from right to left.
However, the Unicode standard is also used in computer encoding. So nothing prevents a hacker from using these invisible characters to manipulate the source code. Putting it cleverly, this can cause an unexpected return of a function or convert part of a comment into executable code. Strings can also have a different value than that shown in the displayed code. In short, the possibilities for manipulation are enormous and difficult to determine at present.
In fact, the use of bidirectional characters does not cause any special alert in compilers and development tools. They go completely under the radar.
Obviously, this technology has not been used by hackers. Researchers have scanned more than 7,000 software repositories open source And they didn’t find anything malicious, other than using it to obfuscate the code.
The ball is now in the court of the compiler and developer tool editors. The good news is that it is very easy to correct the depiction, because it is enough to exclude the use of bidirectional characters, except for specific uses altogether. Unfortunately, the ecosystem is not very responsive.
The researchers alerted nineteen organizations, giving them 99 days to deliver the patch. Only half of them did, and the rest drag their feet. Therefore, developers are interested in the correct analysis of the third-party code that they integrate. For example using the “vim” editor that clearly displays bi-directional characters without changing the direction of the text.
Source : Trojan source

“Unapologetic pop culture trailblazer. Freelance troublemaker. Food guru. Alcohol fanatic. Gamer. Explorer. Thinker.”




