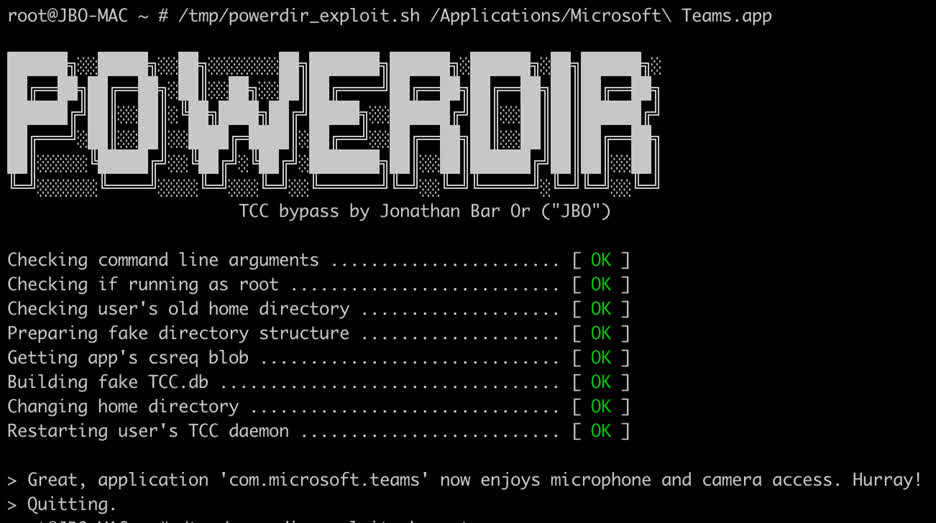
Why it matters: Microsoft on Monday publicly disclosed a vulnerability in macOS that could be used to access or steal sensitive user data. The exploitation is facilitated by a loophole in the TCC framework. The TCC platform is part of macOS that allows users to control which applications can access users’ data, files, and components.
The Microsoft 365 Defender research team called the vulnerability (CVE-2021-30970) “powerdir” after an exploit created by Microsoft researcher Jonathan Bar Or. Microsoft notified Cupertino of the security breach in July 2021 Apple fixed the flaw in December with macOS 11.6 and 12.1.
“We discovered that it was possible to programmatically change the target user’s home directory and create a fake TCC database, which stores the approval history for application requests,” we explained. If exploited on unpatched systems, this vulnerability could allow a potentially malicious actor to orchestrate an attack based on protected personal user data. “
Screen shots show which software grants or accesses the microphone and camera. However, TCC also maintains authorization for other components including screen recording, Bluetooth, location services, contacts, photos, and more.
While Microsoft created the software specifically for this task, any application could use the same technology to exploit the hole. The attacker needs full disk access to the TCC database, which can be granted through other methods. Once acquired, hackers can set or reset access permissions as they see fit.
Powerdir is the third TCC bypass to be found in the last two years. The other two (CVE-2020-9934 and CVE-2020-27937) were revealed and fixed in 2020. Another flaw (CVE-2021-30713) discovered last year across all Apple operating systems allowed attackers to arbitrarily control permissions, which is This allowed hackers to actively exploit it before it was patched in May.

“Wannabe internet buff. Future teen idol. Hardcore zombie guru. Gamer. Avid creator. Entrepreneur. Bacon ninja.”